In recent weeks, the United Arab Emirates has faced a wave of well-publicised hacktivist campaigns, capturing the attention of organisations and their security teams.
Among the prominent groups involved are believed to be Killnet and their affiliate, known as Anonymous Sudan. Both groups are known for their political views.
In this article we look at the growing trend of hacktivism in the UAE, focusing on the activities of Killnet and Anonymous Sudan, while offering valuable insights and recommendations to protect your organisation.
Who are Killnet and Anonymous Sudan?
Killnet and Anonymous Sudan have made their presence known through multiple high-profile cyber-attacks in the UAE, primarily targeting organisations that they class as adversaries.
‘Since establishing their official Telegram channel on January 18th 2023 Anonymous Sudan regularly post their intent to attack those who target Sudan, often resorting to distributed denial-of-service (DDoS) attacks to disrupt the infrastructure of their targets.
These attacks are often resulting in severe disruptions to online services, leading to potentially financial losses, reputational damage, and compromised customer trust.’ – Aaron Hambleton, Director for Middle East & Africa, SecurityHQ
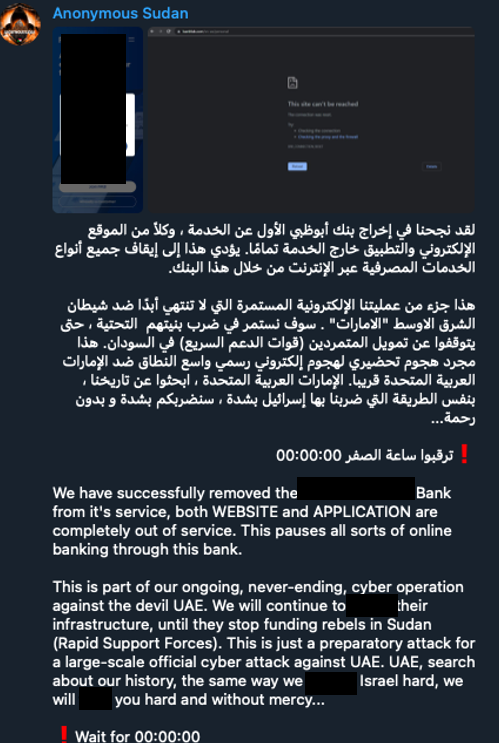
In a recent development, Anonymous Sudan have claimed to have targeted the websites and application of a popular bank. In the post made by Anonymous Sudan, they state the following:
“We have successfully removed the First [redacted] Bank from it’s service, both WEBSITE and APPLICATOIN are completely out of service. This pauses all sorts of online banking through this bank.
This is part of our ongoing, never-ending, cyber operation against the devil UAE. We will continue to [explicit language] their infrastructure, until they stop funding rebels in Sudan (Rapid Support Forces).
This is just a preparatory attack for a large-scale official cyber attack against UAE. UAE, search about our history, the same way we [explicit language] Israel hard, we will [explicit language] you hard and without mercy… Wait for 00:00:00”
See their full telegram post below.
With their Telegram channel serving as a public platform to announce and discuss their attacks, analysing the group’s activity provides valuable insights into their escalating operations.
Hacktivist groups often rely on communication channels like Telegram to disseminate information, coordinate attacks, and rally support. By actively engaging in discussions and sharing updates within their followers via their Telegram channel, Anonymous Sudan seeks to amplify their message and gain traction among its supporters.

Why You Should Care About this Attack
According to the Cyberexpress ‘the notorious Anonymous Sudan has attacked UAE banks. They have fallen victim to the group’s onslaught on a probable spree of DDoS’.
These attacks appear to be a combination of various volumetric DDoS attacks that were designed to overwhelm internal network capacity and even centralized DDoS mitigation scrubbing facilities with significantly high volumes of malicious traffic.
Banks and Financial institutions need to be aware of this group, and how to enhance their security posture. For a more in-depth look, download our Whitepaper on the ‘Financial Sector Threat Landscape’ to explore the current threat landscape, the techniques criminals use to bypass financial security controls.
SecurityHQ’s Recommendations
SecurityHQ’s suggestions to mitigate against attacks:
- Enable rate limiting to restrict requests and prevent overwhelming network and resources.
- Implement IP blocking to identify and block malicious IPs using WAF and threat intelligence.
- Utilize traffic profiling to detect abnormal patterns and triggers for proactive mitigation.
- Enable CAPTCHA or challenges to differentiate between bots and legitimate users, reducing DDoS impact.
- Employ anomaly-based detection to identify abnormal traffic and trigger defensive actions.
Note: For large-scale attacks, additional measures like traffic scrubbing or DDoS mitigation may be beneficial.
Next Steps to Enhance Security Measures
SecurityHQ’s Threat & Risk Intelligence (TRI) service involves the analyses of data, to identify threat actors and vectors victimizing business. It maps your digital footprints with attack tactics to understand the surface exposure from a hacker’s point of view.
View, monitor, prioritise and analyze all digital elements of your organisation, including Internet, applications, systems, cloud, and hardware. Harvest information from the Dark Web, Deep Web, and public domain for complete visibility.
Penetration testing involves simulating an attack on your network surface to identify security loopholes. Hunt for, and highlight, vulnerabilities in your network by emulating real-life external and internal attacks. Testing conducted in a controlled environment, without compromising routine business activities.
If you want to enhance your cyber security posture, reach out to a member of our team, or fill out this form, and our security experts will get back to you.
Instructively, Global MSSP with world-class Security Operation Centers (SOC’s) located around the world, to manage, detect and defend against all malicious activity. Powered by real-time log analytics, security orchestration, automation & response tooling for investigation, threat hunting and response, the company’s 300+ analysts are available to detect, monitor & respond to cyber threats around the clock, to address security risks and challenges, and improve security posture.
By combining dedicated security experts, cutting-edge technology and processes, clients receive an enterprise-grade experience that ensures all IT virtual assets, cloud, and traditional infrastructures, are protected.