June 29, 2017//-As more connected devices link up to the ever-expanding universe known as the Internet of Things (IoT), the wide array of new products envisioned to support the IoT is sure to provide people with tremendous flexibility to control everyday aspects of life, such as picking up the kids with the autonomous vehicle; or being able to remotely control security and temperature—or even irrigation—for houses.
Ideally the expanded convenience offered by these new products will save people time, add to a collective sense of security and improve their overall well-being. Yet there can be a more sinister side to this new broad-based technology, existing in the form of products that are prone to internet counterfeiting and hacking.
Already, semiconductor companies this year have released highly integrated devices to support new IoT products. For instance, new low-power System-on-Chip (SOC) integrated circuits (ICs) support not only wireless protocols but also external sensing and communication technologies—all designed with the latest embedded systems. These new devices are typically available from core circuit devices such as microprocessors, microcontrollers and peripheral ICs.
Some examples include Marvell’s IAP220, a low-power application processor (AP) in the IoT-AP family; Bosch’s BMA455, which utilizes sensors in IoT and smart home applications; or Texas Instruments’ CC1310, a wireless microcontroller to enable faster IoT design cycles. There are also development design kits, such as Intel’s Joule 570x, available to speed the design of a new generation of robots, drones and IoT devices. These are but a few examples of the new devices becoming available from many chipmakers.
Unfortunately, as the technology has advanced, so have the skill and sophistication of hackers and their methods. Hacking has progressed significantly—from simple password hijacking, to more sophisticated software attacks via Trojan horse malware potentially lying dormant in devices awaiting activation, to complex physical chip modifications.
Maintaining physical device security is very important to prevent so-called “Shack Attacks”—named as such because the hacks can be accomplished with low-cost commercially available equipment obtainable from stores like the now-defunct Radio Shack. Here a shack attack can utilize the self-testing capabilities of a chip IC to alter a chip’s functional state.
Also dangerous are much more sophisticated “Lab Attacks,” in which hackers have access to laboratory equipment. A lab attack, for instance, can bridge IC chip traces by utilizing costly semiconductor design equipment, such as Focused Ion Beam (FIB) gear, to reroute data to input/output (I/O) or extraction pins, which then allows hackers to obtain security codes, proprietary information or other sensitive data.
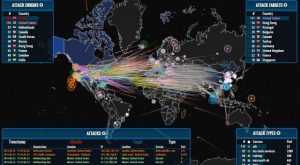
The proliferation of unsecured IoT-connected products and hacking recently emerged in a massive Denial of Service (DDoS) attack on Oct 21, 2016, taking down some internet giants like Netflix, Twitter, Spotify and others in many US locations for most of that Friday morning.
The attacks were traced to DVRs and webcams connected to a malicious botnet. Although no permanent damage occurred, the successful hacking highlights weaknesses in IoT device manufacturing and the tendency for the industry to address security issues after products are released to consumers. Compounding the problem is that IoT device security is dependent on consumers who do not always reset their default passwords or keep their products updated when it comes to security.
Luckily, chipmakers have begun making strides to secure IC devices against counterfeiting and hack attacks. For example, chip “fingerprinting” uses physical unclonable functions (PUFs) built into the chip hardware to uniquely identify a chip’s authenticity. PUFs are widely used in many chips being built today, and new reference designs—such as Maxim’s MAXREFDES143# for IoT security, built to protect an industrial sensing node by means of authentication and notification to a web server—is also an example of more advanced security methods available to design engineers.
However, even this authentication technology can be susceptible to hacking. Take the example of radio-frequency identification (RFID) chips, initially designed to change security codes after each transaction, based on an authentication process to a remote server. RFID chips have now been discovered as susceptible to side channel attacks, in which hackers analyze patterns of memory access or fluctuations in power usage when a device is performing a security-code update. Hackers discovered that by repeatedly cycling off the chip power, they could expose the current security code before a new code was issued.
To counter this weakness, RFID chips have since been developed with onboard power supplies, in order to allow the chips to retain data and complete the security-code change process before loss of power. Still, the example shows that even secure technology like authentication can prove vulnerable in the hands of determined hackers.
With all the rapid advances in technology and threats, readers may ask how they can best protect their products.
My best advice is to:
- Always buy from an authorized distribution source. Make sure you have good and reliable information from authorized distribution sources, as reiterated.
- Create designs using chips with the latest advances in security, and ensure that you have a good source of the newest part introductions available from original component manufacturers.
- Ensure that physical device inventory is—and has been—secure, especially for core devices. See to it that your customers update their security passwords and settings for any internet-connected products.
- Make certain that you are up to date on semiconductor technology news, which can be found in sites such as: https://technology.ihs.com/Research-by-Market/450482/semiconductors
If forced to buy components on the gray market:
- Create a list of trusted supplies with in-house test equipment. Buy from trusted suppliers only.
- Verify that independent distributors can track components back to their authorized distribution source.
- Report all counterfeit incidents and hacking attempts so that others can become aware of the situation and of any other current challenges.
Greg Wood is Director in the Electronic Parts business at IHS Markit
Technology Blog



